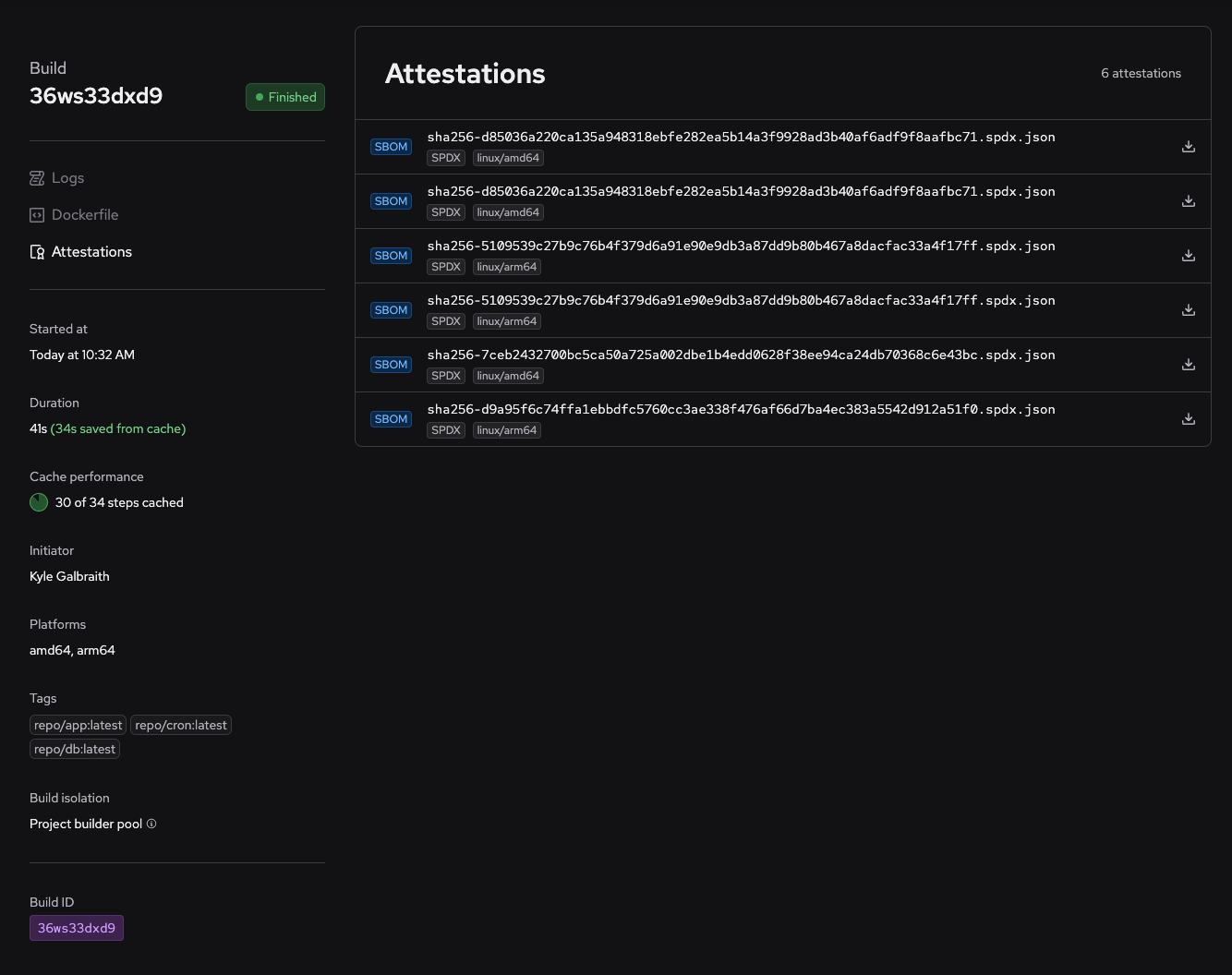
We are excited to introduce our new Attestations feature, which allows you to generate a Software Bill of Materials (SBOM) for every build and easily download it from your build detail view.
Generating an SBOM with Depot
We've added the ability to generate a Software Bill of Material (SBOM) for any depot build or depot bake command via our depot CLI. Add the -sbom=true flag to your build command to generate one for your build.
depot build --sbom=true .
depot bake --sbom=true -f docker-bake.hclWe've also made accessing the SBOMs generated by your build easier. You can specify a directory to write the SBOM(s) to with the --sbom-dir parameter.
depot build --sbom=true --sbom-dir=sboms .
depot bake --sbom=true --sbom-dir=sboms -f docker-bake.hclYou can also access the all SBOMs generated by your build in the new Attestations view as part of our new build insights, where you can download them anytime.
Here, we see that this build was executed via a depot bake command and therefore, we have six SBOMs, one for each target and platform architecture:
SBOMs are generated with Syft, which supports a wide variety of ecosystems, and are saved in the industry-standard SPDX format. You can learn more about the SPDX format here.
Generating SBOMs and uploading them to GitHub
Our depot/build-push-action and depot/bake-action GitHub Actions also support this new SBOM functionality.
With either of our actions, you can specify the sbom parameter to generate a Software Bill of Materials during the build and the sbom-dir parameter to output the generated SBOMs to a specified directory.
From there, you can upload the SBOMs as artifacts via actions/upload-artifact, or you can also submit them to GitHub's dependency submission API via advanced-security/spdx-dependency-submission-action. This allows you to receive Dependabot alerts for vulnerabilities in the contents of the built image itself!
jobs:
docker-image-sbom:
steps:
- name: Checkout repo
uses: actions/checkout@v3
- name: Set up Depot CLI
uses: depot/setup-action@v1
- name: Build an image with Software Bill of Materials (SBOM)
uses: depot/build-push-action@v1
with:
sbom: true
sbom-dir: ./sbom-output
- name: upload SBOM directory as a build artifact
uses: actions/upload-artifact@v3.1.0
with:
path: ./sbom-output
name: 'SBOM'
- name: upload spdx dependency
uses: advanced-security/spdx-dependency-submission-action@v0.0.1
with:
filePath: ./sbom-output/Note: When you upload an SBOM to GitHub's dependency submission API, it will be uploaded as a dependency manifest. So, you will receive Dependabot alerts for the packages included in the SBOM.
Generate an SBOM today
We're excited about incorporating SBOMs and future attestations into Depot, especially considering their growing importance in supply-chain security.
We'd love to hear your feedback and ideas on how we can make this even better. You can head to our Discord Community and let us know your thoughts.
If you're new to Depot, you can sign up for free and get up to 40x faster Docker builds in just a few minutes.